Should You Be Concerned About Third-Party Risk in the Cloud?
October 4th, 2022 | 3 min. read
%20(48).jpg)
Almost everyone is on the cloud – you, your providers, your partners, and even your clients. That's because there's been a tectonic shift in working patterns since the pandemic. In just the past few years, thousands of businesses have become more dependent on the cloud for critical day-to-day operations. The technology allowed companies to shift toward remote work and keep operating despite lockdowns.
Unfortunately, it's not a risk-free endeavor. The sudden shift and reliance on cloud services come with many unintended consequences. For one, many companies that moved implemented large-scale structural changes quickly to survive extended lockdowns. Doing hasty migrations leaves many security gaps and issues that could lead to major incidents. And, since everyone's on the cloud, your business is more vulnerable to third-party risks.
Intelligent Technical Solutions (ITS) is an IT support company that has provided hundreds of businesses with secure cloud services. We are dedicated to helping you secure your data no matter where you decide to store it. In this article, we'll dive into why you should pay more attention to third-party risks in the cloud by discussing the following:
- Why You Should Worry About Third-Party Risk in the Cloud
- Issues to Consider About Third-Party Cloud Security
- How to Secure Your Cloud from Third Party Risk
Why You Should Worry About Third-Party Risk in the Cloud
Cloud computing has been invaluable in enabling teams to collaborate from anywhere across the world. However, that boon might also be its Achilles heel. Because while it allows you and your suppliers to access data easily, that's also true for cybercriminals.
Recently, Proofpoint, Inc. collaborated with the Cloud Security Alliance (CSA) to produce a study titled Cloud and Web Security Challenges in 2022. The report surveyed over 950 IT and security professionals representing various industries and organizational sizes.
One of the most notable findings in the study is that more than half (58%) of respondents had third-party partners and suppliers that experienced cloud-based security incidents in 2021. Equally troubling is that while a majority (81%) of respondents said they are moderate to highly concerned about third-party risks, only 36% of them had data loss prevention (DLP) solutions in place.

Source: Cloud and Web Security Challenges in 2022 Study
It signifies that concerns regarding third-party risks in the cloud are warranted and that a majority of businesses aren't prepared for it.
How to Secure Your Cloud from Third-Party Risk
You may not have a lot of control when it comes to how your suppliers handle their cloud security. However, that doesn't mean there's nothing you can do to protect your business. Check out some activities you can take to secure your cloud from third-party risk:
Vendor Risk Assessment
Ensuring trust between you and your suppliers is not always an easy task. That's why preparing a complete risk profile is critical before partnering with a vendor.
You can achieve that by asking yourself the following:
- What data will the vendor have access to?
- What operations and functions will they be responsible for?
- How can it impact your operations if the vendor experiences a security incident?
In some cases, you can even ask the supplier to complete a vendor risk questionnaire. From that, you should be able to learn what security policies and practices your supplier has in place.
Overall, your vendor risk assessment activities should take your compliance obligations into consideration.
Strict Shadow IT Control
Shadow IT refers to the use of any type of IT service, application, hardware, or software that anyone on your team procures and manages without the knowledge of the IT department. In short, it's any application that a team member downloads without asking your tech guys first. In the context of this article, however, we will be referring to cloud shadow IT.
The biggest problem with cloud shadow IT is its prevalence, which can involve third-party services, add-ons, extensions, and integrations. Unfortunately, a lot of them come with inconsistent or insufficient security controls. That poses a serious third-party risk, and it's hiding right under your security team's nose.
While it's been said that you can't fully eliminate shadow IT, you can slow it down and mitigate its spread across your network. You can do that by creating strict shadow IT control policies, educating your team, and opening the lines of communication between your staff and IT. Doing that will help your IT team manage and secure those third-party services or find a better alternative.
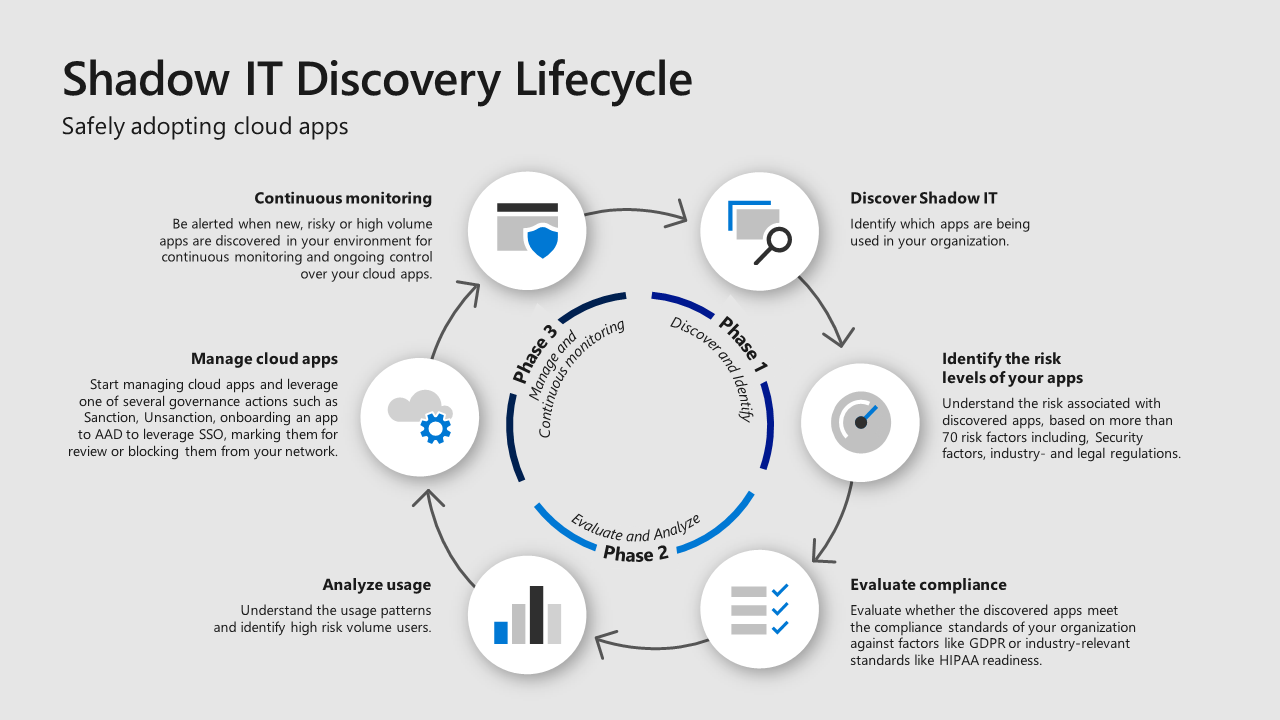
Source: Microsoft
Identity and Access Management (IAM) Policy
A strong IAM policy is a critical component of risk mitigation and should come as a standard for any cloud service deployment. Controlling who gets access to what by using privileged access management is a good example of a solid IAM policy. That helps ensure your activities in the cloud are restricted only to those who really need it, minimizing your attack surface.
Monitor Misconfigurations
Managing the security settings of your cloud service is part of your shared data protection responsibility. If you are on a public cloud or any software-as-a-service (SaaS) environment, you should monitor the configuration of your settings; a misconfigured cloud service could cause a security vulnerability that attackers can exploit.
Ready to Reduce Third-Party Risk in the Cloud?
Almost all of your suppliers and third-party partners leverage the benefits of the cloud in some form or another. Unfortunately, not everyone is utilizing the technology securely, which opens you up to third-party risk.
Thankfully, there are some things you can do to protect your data in the cloud, such as:
- Completing a vendor risk assessment
- Implementing strict shadow IT controls
- Using a strong IAM policy
- Monitoring for cloud misconfigurations
At ITS, we help secure your environment from different kinds of threats and mitigate third-party risk with robust managed cybersecurity services. Learn more about the truth behind common misconceptions regarding cloud security by reading our article titled Why Cloud Storage Needs Additional Security?
Mark Sheldon Villanueva has over a decade of experience creating engaging content for companies based in Asia, Australia and North America. He has produced all manner of creative content for small local businesses and large multinational corporations that span a wide variety of industries. Mark also used to work as a content team leader for an award-winning digital marketing agency based in Singapore.
Topics:
