Common Causes of Security Gaps in Your Network & How to Resolve Them
August 3rd, 2022 | 5 min. read

As companies adopt remote and hybrid working environments, it has become common for employees to use personal devices like laptops and phones to read emails and access files. This practice results in more applications and websites being accessed during work hours, consequently exposing your employees and company network to many possible security vulnerabilities.
In turn, these risks create gaps in your cybersecurity and cause damage.
That is why it’s important to control and manage all the devices connected to your network by implementing a security system with multiple layers of protection. In addition, you must be knowledgeable of the common causes of security gaps in a business network to avoid or resolve them.
At ITS, we’ve received hundreds of calls regarding poor cybersecurity. What we do as a Managed IT Service Provider with a key focus on cybersecurity is monitor the client’s environments for potential threats and vulnerabilities to help find a suitable solution. We’re able to resolve as many issues, and we will continue to help businesses bolster their cybersecurity.
In this article, you will learn:
- Most common causes of security gaps in a business network
- Best security systems that can help fill the security gaps
What are the most common causes of security gaps?
According to Edward Griffin, a Partner at ITS San Francisco, a successful threat management system must encompass the great triumvirate of secure digital transformation–people, process, and technology.
Griffin mentioned that if one of the three pillars do not work as intended, the whole thing will collapse.
On that account, we list down the things that can harm any of the three:
On the people side, the lack of security awareness training is a significant factor. Unfortunately, many businesses don’t do enough of that.
“It doesn’t matter what we build on the perimeter or what we build in terms of security policy and procedure; if you have a user blindly clicking on things and opening up attachments without any discretion, it will be detrimental to the business.” Griffin explains.
On the processes side, not having a predefined action to a particular incident or the lack of team members' understanding of how they fit into the business process plays a huge part. To put it simply, the unpreparedness of the organization; and failing to expect and respond to breaches will come at a high cost.
On the technology side, it could be the lack of implementation of common security tools such as:
- Multi-factor authentication (MFA) for centralized identity management
- Single sign-on (SSO) to minimize the sprawl of accounts throughout the internet
- Firewalls. Or it could be that they have firewalls, but it’s not fully utilizing the next-generation firewall features
What are the best systems that can help fill the security gaps?
Is there one thing that can give you a hundred percent security? The answer is none.
“As we are well on our way to Zero Trust design, you have to assume breaches no matter how sophisticated your IT infrastructure is.” Griffin says.
This way, you are always on your toes for possible attacks.
In terms of protection, however, the only way to build and enhance your security is to layer your defenses.
“You don’t just rely on one thing but multiple things. But even these may not bring you 100% protection; it only reduces the economic opportunity for the attacker.”
If you’ve got multiple layers of protection and cyber attackers are forced to crack each layer in order to access your assets, they will soon tire themselves out and hopefully give up. That’s the best-case scenario.
You are trying to make it economically unfeasible for attackers to profit from a compromise of your environment.
So, going into the said layers. There are two types of security systems you will need: Endpoint and Perimeter.
1. Endpoint Protection
Endpoint protection involves the use of comprehensive and advanced solutions to secure endpoints connected to corporate networks. Endpoints refer to end-user devices like laptops, desktops, and mobile phones. They serve as access points to your company's network and can be exploited by cybercriminals to launch attacks.
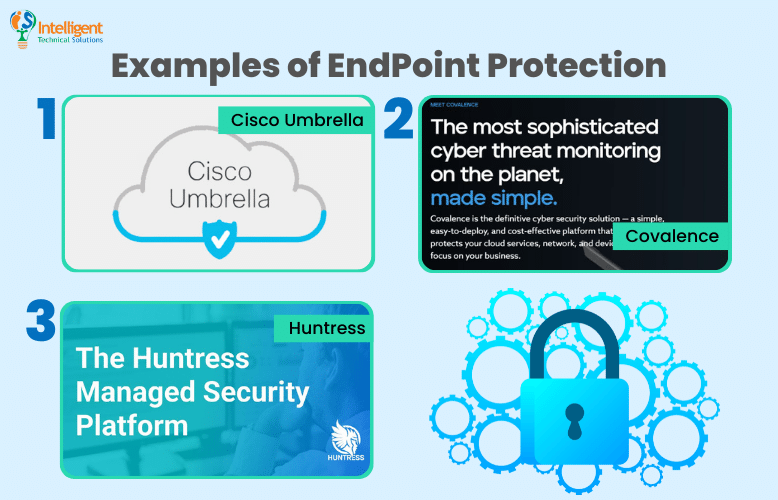
Following are some examples:
Cisco Umbrella
Cisco Umbrella is a cloud security solution that protects devices connected to your network against internet-based threats. It helps prevent data exfiltration by blocking the data transmission to unwanted destinations and cloud malware by scanning cloud-based apps swiftly so you can detect and stop infections before they spread.
Covalence
Covalence combines the use of algorithms, machine learning, and analytics to monitor, detect, and respond to threats in cloud networks and endpoints. It focuses on monitoring and managing your systems (e.g., laptops and servers) and cloud-based accounts (e.g., email and storage system).
Its built-in DNS firewall allows you and your employees to browse online safely by blocking connections to malicious websites.
Huntress
Huntress is a threat detection and response platform that protects small businesses from threats like malicious footholds and ransomware. Its team of experts is available 24/7 to find and stop sophisticated attacks on companies' networks. They assess suspicious activities and inform clients in case of verified threats to avoid the stress that comes with false negatives or positives.
Huntress involves the use of endpoint protection, detection, and response solutions in one interface.
2. Perimeter Security
A perimeter refers to the border between networks, like your company's private network and the public internet. Like most security systems, perimeter security covers surveillance detection, pattern analysis, and threat recognition and control. It involves securing a company's network from hackers attempting to intrude its systems.
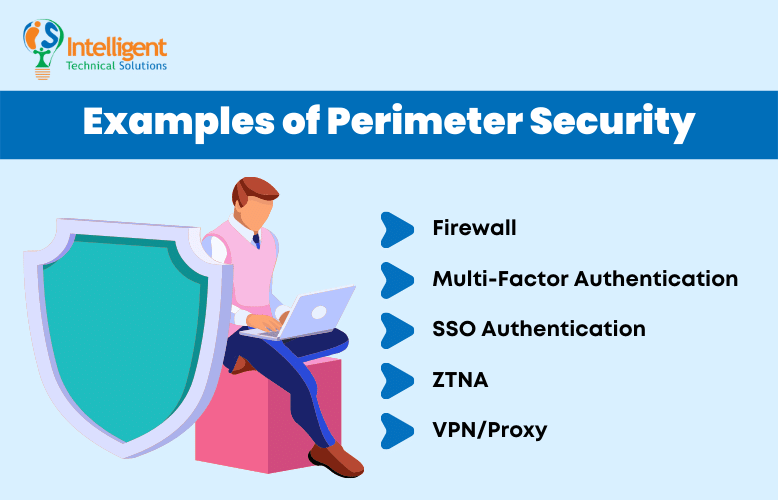
To keep your private network protected from web-based threats, your IT team can set up a perimeter security system that comprises various components, including:
Firewall
A firewall monitors and controls traffic to and from your network. It’s a barrier between your corporate network and an untrusted network like the internet that filters data packets based on a predetermined set of security rules.
Multi-factor Authentication
MFA offers an additional layer of protection to prevent unauthorized people from accessing an account or data. When logging in to an account or app, a user will be required to verify their identity further. They may be asked to enter a code sent to their registered phone number or scan their fingerprint.
SSO Authentication
When you’re able to successfully enforce MFA, you may recruit your organization to leverage SSO when possible.
Single sign-on (SSO) is an advanced authentication technology that enables you to log in to multiple applications and websites using a single login credential. An SSO solution creates authentication tokens whenever users sign in. An authentication token contains data stored in a user's browser or within the SSO solution's server. The apps that the user accesses will verify with the SSO platform.
ZTNA
Zero trust network access comprises technologies that allow remote users to access private applications securely.
Unlike VPNs, where users can access anything on a network once they are granted access, ZTNA follows the “never trust, always verify” model. This means that access is given only to those who need it, and users are verified continuously while they are connected to the apps.
VPN/Proxy
In any case, a ZTNA is still not feasible, have a proxy or VPN requirement to ensure that you don’t have assets just hanging off the internet.
VPNs encrypt your data, which makes information like CC account numbers inaccessible to hackers. On the other hand, proxies allow you to connect to a website or app through an outside host server. Both hide your identity, location, and IP address while browsing the web.
Apart from the aforementioned solutions, another thing you can do to help avoid security gaps is to hold regular end-user training. Since 95% of cyber incidents are primarily caused by human error, the key is to train your team members in cybersecurity.
You may organize phishing campaigns where you send a fake phishing email against an organization and find out where your weak points are through that. Or you may also conduct phishing training to explain what to look forward to in phishing emails.
“It keeps coming down to people. As good as we are building up a security architecture, it can be compromised in a second by one accident.” Griffin states.
Does your business network have security gaps?
Remote working is here to stay, and so are the potential threats that come with it. The only thing you can do to lessen the damage is to have multiple layers of security up in your network. As a recap, here are the best security systems that can fill the security gaps:
- Endpoint protection
- Firewall
- MFA
- SSO authentication
- ZTNA
- VPN/Proxy
Here at ITS, we help hundreds of businesses strengthen their network defenses, especially in a remote work setup. Get a free cybersecurity assessment with us today if you want to know more about these security systems, as well as your current IT environment.
Jess is a Content Writer who commits herself to creating helpful, relevant, and easy-to-digest technical articles. When she isn't writing, she devotes her energy (and money) to collecting K-Pop photo cards, which she likes to call an 'investment.'
Topics:
