What is EDR, and Why Does My Business Need One? [Updated]
February 22nd, 2024 | 4 min. read

Editor's note: This post was originally published on January 10, 2022and has been revised for clarity and comprehensiveness.
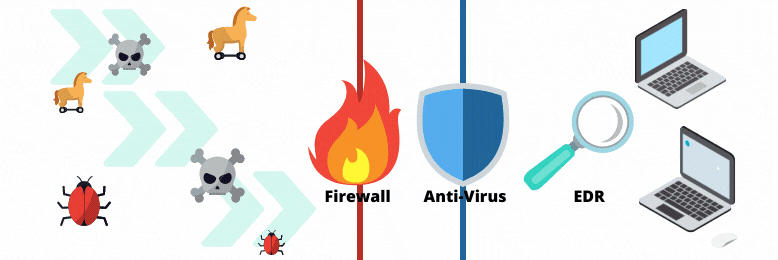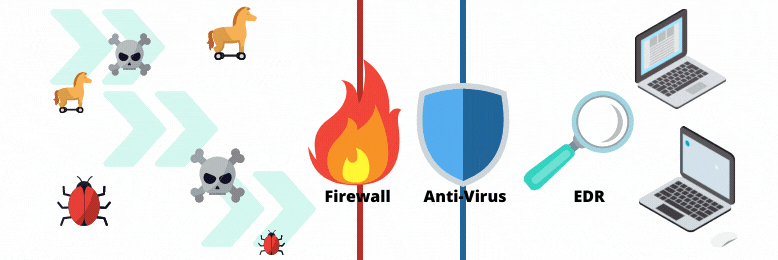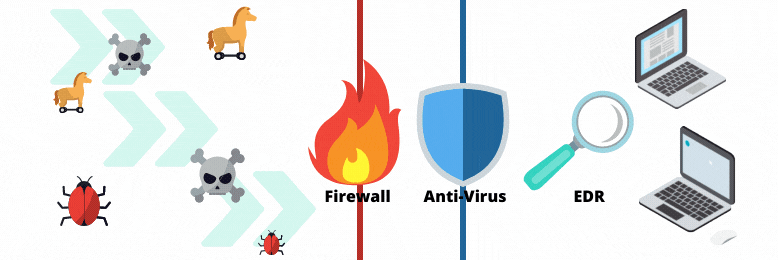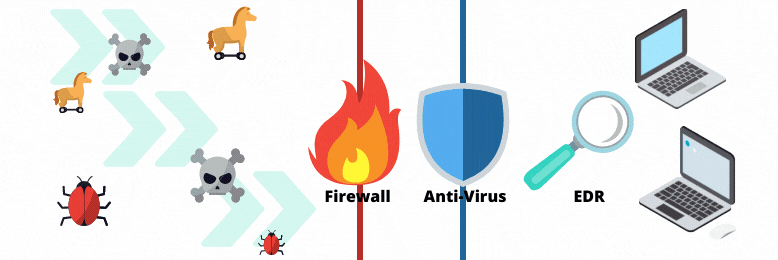
Your organization already has antivirus and a firewall; what more could you need? It’s tempting to think that having those tools is enough to help you sleep soundly, knowing your entire network is protected.
Unfortunately, cyber threats continue to grow in complexity and sophistication. It's either you keep up or suffer the consequences. Threat actors can penetrate both antivirus and firewalls with a well-constructed phishing email or social engineering trick. Cybercriminals already know that you have defenses in place, and those threat actors will find ways to get around them.
So, how do you protect your network once hackers get through your first line of defense? That’s where Endpoint Detection and Response (EDR) solutions come in.
At Intelligent Technical Solutions (ITS), we’ve helped hundreds of businesses bolster their cybersecurity efforts. From our experience, EDR is a vital piece of the cybersecurity puzzle. To help you understand why you need one, we’ll discuss the following topics:
What is EDR?
Endpoint Detection and Response (EDR) is an integrated endpoint security solution that combines real-time continuous monitoring and collection of endpoint data. It uses its rules-based automated response and analysis capabilities to monitor activity data that might indicate a threat.
“EDR effectively replaces antivirus and is just better than the next generation antivirus,” said Rob Schenk, ITS Cybersecurity Advisor.
Simply put, while your firewall and antivirus are trying to prevent intruders from breaking into your network, EDR watches for threats lurking inside it. It monitors all the devices connected to your network, looking for any suspicious activity.
EDR tools can also analyze the data to identify patterns and automatically respond to threats by either removing or containing them or alerting security personnel. They can also be used as forensics tools to help you investigate how an attack occurred.
Why Do You Need EDR?
Implementing EDR security can bring a lot of advantages to your organization. Here are the main EDR benefits you should know:
1. Prevents Data Breaches

Many small business owners underestimate the value of their data. However, a data breach has the potential to be a very costly affair that could cripple organizations. In a study by IBM and the Ponemon Institute, researchers found that the average cost of a data breach in 2023 is $4.45 million, a 2% rise from their 2022 findings—a staggering amount, especially for a small business.
What’s worse is that the number of incidents is continuing to increase. According to the Identity Theft Resource Center (ITRC), the number of data breaches reported in 2023 exceeded the total for 2022. And those numbers only count the publicly reported ones, not those that went under the radar.
An EDR can help prevent that. A sophisticated EDR system can detect threats in real time, allowing you to stop a breach immediately.
2. Detects Threats that Go Unnoticed

In many of the most high-profile cyber-attacks recorded in the past few years, cybercriminals hid in plain sight for weeks or even months. They establish footholds within your network and bide their time, trying to evade detection and planning their next move.
In IBM’s Cost of a Data Breach report, it was revealed that the average time it took for companies to identify a breach in their network was 204 days. It also took them 73 days to fully contain it, bringing the total “lifecycle” to around 280 days. That’s a lot of time for cybercriminals to scope out your vulnerabilities and cause severe damage.
An EDR is equipped to detect threats that tend to go unnoticed. It utilizes advanced analytics to identify unusual behavioral patterns that might indicate a security breach. It can then alert relevant personnel, allowing you more time to detect and contain a possible breach.
3. Accelerates Incident Response

When it comes to containing a breach, time is essential. It can help prevent attackers from wreaking havoc in your network or mitigate the damage.
An EDR solution can keep track of all interactions between devices in your network, allowing your incident response plan to kick in faster. It also provides:
- Real-time visibility across all endpoints
- Tracking events and processes like logins
- Registry modifications
- Network connections
This will allow your team to investigate any suspicious activity immediately and buy them time to contain a breach.
4. Allows for Proactive Threat Hunting

With an antivirus, you must wait for an alert before your incident response plan kicks in. Having to wait for a threat to pop up is one of the biggest reasons some breaches go undetected for months.
However, with a sophisticated EDR system, you can proactively hunt for threats in your network by monitoring for strange behavior, suspicious activity, and other threat indicators across all endpoints. That gives your cybersecurity team enough information on whether to investigate further, possibly preventing an attack from becoming a breach.
5. Simplifies Endpoint Management
 EDR solutions allow your incident response team to detect, identify, and contain threats from a single centralized platform. That means it doesn’t matter where the device is located; your security team can respond to a potential attack or breach.
EDR solutions allow your incident response team to detect, identify, and contain threats from a single centralized platform. That means it doesn’t matter where the device is located; your security team can respond to a potential attack or breach.
6. Cost-Efficient
![]() Some automated EDR processes can help minimize the workload of detecting and responding to threats. It allows your security team to save time and resources as it reduces the need to monitor multiple tools and dashboards constantly. That also helps create a more integrated security information and event management (SIEM) system.
Some automated EDR processes can help minimize the workload of detecting and responding to threats. It allows your security team to save time and resources as it reduces the need to monitor multiple tools and dashboards constantly. That also helps create a more integrated security information and event management (SIEM) system.
Ready to Setup an EDR for Your Workplace?
EDR solutions offer many benefits that can improve how you detect and respond to cyber incidents. It not only helps you enhance your cybersecurity, but it can also save you time, money, and resources. A robust security system requires multiple layers of protection, and an EDR solution is a vital part of that.
At ITS, we’ve helped clients choose and implement sophisticated cybersecurity tools like EDR. Learn more ways to boost your network security by checking out the following resources:
Mark Sheldon Villanueva has over a decade of experience creating engaging content for companies based in Asia, Australia and North America. He has produced all manner of creative content for small local businesses and large multinational corporations that span a wide variety of industries. Mark also used to work as a content team leader for an award-winning digital marketing agency based in Singapore.
Topics:

