What is CMMC 2.0 and Does Your Business Need One?
July 1st, 2022 | 4 min. read

If your business is part of the Department of Defense’s (DoD) supply chain as a defense contractor or subcontractor–or you have plans to be in the future– then yes. You must be CMMC-certified to qualify for bidding on a government contract.
But what exactly is CMMC 2.0, and what can you do to get the certification? We previously talked about what you can expect when applying for a CMMC as a business owner, but a lot has changed since then.
At Intelligent Technical Solutions (ITS), we help hundreds of businesses stay on top of the latest cybersecurity practices and compliance standards. In this article, we’ll answer the following important questions:
- What is CMMC?
- How is CMMC 2.0 different from the previous model?
- What are the levels of CMMC 2.0?
- How to prepare for the CMMC 2.0 Compliance?
- How can an MSP help you with your CMMC 2.0 certification?
What is CMMC?
We reached out to Peter Swarowski, ITS’ Operations director, to explain what CMMC is. He says,
“CMMC or Cybersecurity Maturity Model Certification is a government certification that the Department of Defense (DoD) contractors need to adhere to. The idea is that the DoD needs its prime contractors to really up its cybersecurity maturity by having a framework and goal they need to achieve to be in a better place, cybersecurity-wise.”
This certification is essential to the DoD considering the huge amount of sensitive data they have to protect, specifically the FCI and CUI.
- Federal Contract Information (FCI)
The federal government protects information regarding its contracts—both details generated by the government and those provided by contractors. - Controlled Unclassified Information (CUI)
“CUI is information that is not classified from a defense standpoint but is important and needs to be protected,” Swarowski says. It encompasses any data that is sensitive in nature but that does not require federal clearance to access. This includes personally identifiable information, technical drawings, legal documents, and other intellectual property.
Overall, CMMC has allowed private organizations to work with the federal government without putting a huge amount of data at risk. However, with the evolving threats in the cybersecurity landscape, the government realized the need for a more stringent compliance model.
Hence, the creation of the CMMC 2.0.
How is CMMC 2.0 different from the previous model?
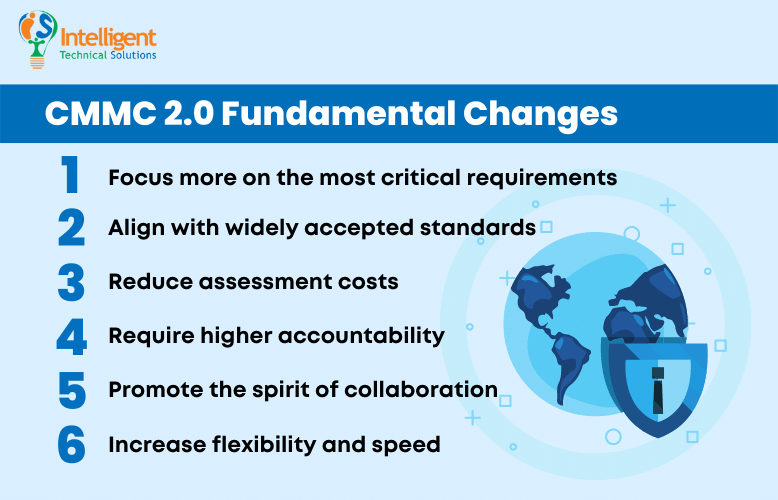
In essence, CMMC 2.0 focuses on streamlining the model, reducing costs for contractors, and aligning current cybersecurity requirements with new federal requirements. The Department of Defense (DoD) lists down the fundamental changes.
CMMC 2.0 will:
- Focus more on the most critical requirements
Probably the most apparent modification, CMMC 2.0, streamlines the model from 5 to 3 compliance levels. We’ll talk about each level later on. - Align with widely accepted standards
CMMC 2.0 uses National Institute of Standards and Technology (NIST) cybersecurity standards. - Reduce assessment costs
It allows all companies at Level 1, and a subset of companies at Level 2 to demonstrate compliance through self-assessments. - Require higher accountability
Increases oversight of professional and ethical standards of third-party assessors. - Promote the spirit of collaboration
The updated model also lets companies, under certain limited circumstances, make Plans of Action & Milestones (POA&Ms) to achieve certification. - Increase flexibility and speed
Finally, it allows waivers to CMMC requirements under certain limited circumstances.
These changes will all be implemented under clause 252.204-7021. The government will require 9-24 months for the rulemaking process, providing incentives for contractors who will voluntarily obtain a CMMC certification in the interim period.
What are the levels of CMMC 2.0?
The updated CMMC program structure narrows down the number of levels from five to three by doing away with the transition levels 2 & 4. The aim is to simplify the program both for the contractors and the DoD and focus more on the things vital to National Defense. Below are the new levels in CMMC 2.0:
 1. Level 1 (Foundational)
1. Level 1 (Foundational)
This level is the same as the original Level 1 and only applies to companies that focus on FCI protection. It follows the most basic cybersecurity practices based on the 17 controls found in FAR 52.204-21 or the Basic Safeguarding of Covered Contractor Information.
These controls protect covered contractor information systems and limit access to authorized users.
 2. Level 2 (Advanced)
2. Level 2 (Advanced)
Compliance with Level 2 is applicable to companies working with CUI. It is comparable to the old CMMC Level 3, with requirements that mirror NIST SP 800-171.
This eliminates all practices and maturity processes unique to CMMC 1.0 and aligns with the 14 levels and 110 security controls developed by the National Institute of Technology and Standards (NIST) to protect CUI.
 3. Level 3 (Expert)
3. Level 3 (Expert)
The highest level of the CMMC 2.0 Model focuses on reducing the risk from Advanced Persistent Threats (APTs). It is designed for companies working with CUI on DoD’s highest priority programs and can be compared to the old CMMC Level 5.
While there is still no final list, DoD said that the requirements for this level would be based on NIST SP 800-171’s 110 controls plus a subset of NIST SP 800-172 controls.
How to prepare for the CMMC 2.0 Compliance?
The process to achieve a certain level of certification takes up to twelve months or more and requires the company's active participation to achieve and maintain compliance. You will need to have what you can call an accountability partner so you wouldn’t miss a step.
“The contractors will have to reach out to a registered provider (RP) to understand what they need to have in place to pass the certification,” Swarowski explains.
RPs provide pathways such as consultation and recommendations and help you implement these measures to prepare for the CMMC certification:
- Assess your current organization for NIST 800-171 compliance. Regularly check and assess if the security controls in your organizational systems are effective in their application.
- Create or update your System Security Plan (SSP). NIST 800-171r2 mandates contractors to document and update SSPs, including, but not limited to, company policies, network diagrams, and relationships with other systems.
- Build the POA&M. The POA&M will document the remediation project plan and help establish timelines and resource requirements.
- Once successful, implement the said Remediation Plan. This will ensure compliance with NIST 800-171r2 and existing contracts while preparing for the full CMMC rollout.
- The last step is to maintain compliance. Maintaining compliance with DoD security standards can be a complex undertaking and is often overlooked, but it is the most critical part. It requires a documented plan and frequent activities to ensure controls are followed.
How can an MSP help you with your CMMC 2.0 certification?
Given the complexity of the processes you need to carry out to achieve this certification, it may take too much time and resources, especially for small to medium-sized businesses. For such instances, the help of a reliable and expert service provider might be more beneficial in the long run.
As a Managed IT Service Provider (MSP), ITS has the necessary tools and assets to help assess and create a security and remediation plan. Swarowski enumerated the things that an MSP such as ITS can do now to avoid cramming for the certification, and that includes running a gap analysis to see what you already have in place and what you don’t–and then filling the gaps to get to a certain level.
In addition, ITS also helps monitor the process, resolves issues, and provides detailed reporting so you will be kept in the loop on the progress. Schedule a free network assessment with us today to start your CMMC journey.
Jess is a Content Writer who commits herself to creating helpful, relevant, and easy-to-digest technical articles. When she isn't writing, she devotes her energy (and money) to collecting K-Pop photo cards, which she likes to call an 'investment.'
Topics:
