Cyber Incident Reporting for Critical Infrastructure Act of 2022
July 11th, 2022 | 4 min. read

If one of your team members experiences a cyber incident, you would want them to reach out and share that information with you. Wouldn’t you? It allows you to tap on the right people to respond to the situation, contain it and prevent it from causing further damage. That act of self-reporting is for the collective good of everyone. The Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA) has the same reasoning behind it.
Cybersecurity information sharing is an essential part of the collective defense and security of everyone. The process used to be voluntary, which means a lot of incidents go unreported. However, because of CIRCIA, it’s now a formal legal requirement. That means, if you’re part of any industry in critical infrastructure, you are required to submit information on any cyber incidents you encounter.
That’s great news for US cybersecurity in general, but what does that mean for your organization?
At ITS, we are a security-focused managed service provider (MSP) dedicated to helping businesses understand the current cybersecurity landscape. In this article, we’ll break down what you need to know about CIRCIA by discussing the following topics:
- What is CIRCIA?
- What Types of Activity Should You Report?
- What Information Do You Need to Report?
- How Will You Report Cyber Incidents?
- What Industries are Affected?
- What Does the New Law Mean for Your Organization?
What is the Cyber Incident Reporting for Critical Infrastructure Act of 2022?

The Cyber Incident Reporting for Critical Infrastructure Act of 2022 is a law passed by the US federal government in March 2022. It mandates organizations involved in critical infrastructure to report security incidents to the US Cybersecurity and Infrastructure Security Agency (CISA). The law requires that a report is made within 72 hours of discovering an incident and 24 hours if the victim makes a ransomware payment.
CIRCIA was created in response to the recent spike in cybercrime. It aims to empower CISA to collect and disseminate information on new threats to help strengthen cybersecurity across the country. Despite how intimidating the new law sounds, It can actually help alert you to new cyber-attacks, patches, and solutions. That will allow you and others to respond more effectively to emerging threats.
What Types of Activity Should You Report?
Under the new law, organizations should notify CISA when they experience an incident involving at least one of the following:
- Unauthorized access to your system
- Denial of Service (DOS) attacks that last more than 12 hours
- Malicious code on your systems, including variants if known
- Targeted and repeated scans against services on your systems
- Repeated attempts to gain unauthorized access to your system
- Email or mobile messages associated with phishing attempts or successes
- Ransomware against critical infrastructure (must include variant and ransom details if known)
What Information Do You Need to Report?
As of this writing, the law has yet to take full effect. That means the guideline for what information you will be legally required to share is still pending. However, CISA has provided the bare minimum information they want from you should you encounter a cyber incident. However, the agency can also request more information in certain cases.
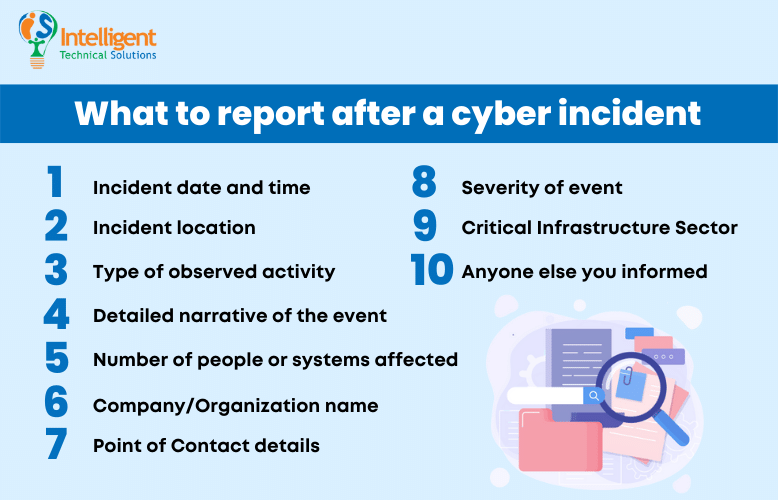
Take a look at the 10 key elements you need to share:
- Incident date and time
- Incident location
- Type of observed activity
- Detailed narrative of the event
- Number of people or systems affected
- Company/Organization name
- Point of Contact details
- Severity of event
- Critical Infrastructure Sector, if known
- Anyone else you informed
While it might be alarming to some to provide the information above, knowing it may be shared publicly, CISA has stated that it will anonymize the victim’s information. The main purpose of disseminating the information is not to penalize a company for an attack. Rather, it’s to warn others and help them manage their risk.
How Will You Report Cyber Incidents?
Now that you know what to report let’s discuss the reporting methods. Many Federal and Critical Infrastructure partners have completed one of CISA’s Incident Reporting Forms. If your organization has already done one, then CISA advises that you continue using those forms in the future to report incidents.
However, if you have yet to report to CISA before, you can also send an email to Report@cisa.gov. Try to be as detailed as possible, making sure to provide the 10 key elements mentioned above.
CISA is also partnered with the Anti-Phishing Working Group (APWG). It’s an organization that collects phishing emails, mobile messages, and websites to help warn people from such scams. You can share phishing info with CISA by sending the phishing email to phishing-report@us-cert.gov.
What Industries are Affected by CIRCIA?

The new law applies to businesses that maintain or manage what the US government calls critical infrastructure. For now, CISA has the leeway to interpret what critical infrastructure means, so a variety of businesses across many industries might be covered by that definition.
At the very least, CISA will likely be looking at businesses that cover the sixteen sectors currently defined as “critical infrastructure” industries under Presidential Policy Directive 21. These include the following:
- Chemical
- Commercial Facilities
- Communications
- Critical Manufacturing
- Dams
- Defense Industrial Base
- Emergency Services
- Energy
- Financial Services
- Food and Agriculture
- Government Facilities
- Healthcare and Public Health
- Information Technology
- Nuclear Reactors, Materials, and Waste
- Transportation System
- Water and Wastewater Systems
Just to reiterate, CISA may choose to add or omit industries in this list based on their interpretation of organizations covered under critical infrastructure. It is by no means the definitive list; it’s more of a general guideline of who may or may not be covered by the new law.
What Does CIRCIA Mean for Your Organization?
While we haven’t experienced the full impact of the new law, it’s safe to assume that there will be significant changes that need to occur across all the industries covered by the law.
For one, you will need to beef up your cyber detection and monitoring capabilities. If an incident does occur (and it most likely will), those tools will help you conduct investigations more efficiently. In addition, you might want to pick team members who have the technical expertise to handle the forensic investigation as well as generate the report.
If you don’t have the right people for the job, you can always seek help from security-focused IT support companies. They can provide you with advanced managed cybersecurity solutions that help you detect and monitor threats and prevent attacks.
Is Your Business Ready to Comply with CIRCIA?
CIRCIA will require any business defined as critical infrastructure to self-report any cyber incidents to CISA. The new law was enacted to significantly improve CISA’s cybersecurity information network. That will allow them to do the following:
- rapidly deploy resources and assist victims suffering attacks
- analyze incoming reporting across sectors to spot trends
- and quickly share that information with network defenders to warn other potential victims.
To do that, CISA will need our help. Organizations involved in critical infrastructure will have to report on cyber incidents like unauthorized access to systems, ransomware, phishing, and more. They will also need to provide key details regarding the incident based on CISA’s guidelines. After which, they will need to send a report to Report@cisa.gov within 72 hours of discovering an incident and 24 hours if the victim makes a ransomware payment.
At ITS, we’ve helped businesses comply with new laws and regulations pertaining to cybersecurity. Check out our article entitled: Can an MSP Help You with Regulatory Compliance? After reading, you will learn the top challenges compliance teams face and how IT support companies can help you overcome them.
Mark Sheldon Villanueva has over a decade of experience creating engaging content for companies based in Asia, Australia and North America. He has produced all manner of creative content for small local businesses and large multinational corporations that span a wide variety of industries. Mark also used to work as a content team leader for an award-winning digital marketing agency based in Singapore.
Topics:
