6 Most Dangerous Types of Phishing Scams to Watch Out for
September 15th, 2020 | 4 min. read

Phishing accounts for over 30 percent of breaches and remains the biggest threat to small businesses. Learn more about the 6 most dangerous types of Phishing Scams to watch out for, and how to prepare for them.
According to Verizon’s 2020 Data Breach Investigations Report, phishing accounts for over 30 percent of breaches and remains the biggest threat to small businesses. What’s worse is that phishing attacks are growing even more sophisticated and malicious as many businesses continue to work remotely.
 It’s important that you and your employees know how to spot phishing scams if you want to effectively protect your company data. To get you started, here are the six most common (and most dangerous) types of phishing scams, and some useful tips on how you can defend your business against these.
It’s important that you and your employees know how to spot phishing scams if you want to effectively protect your company data. To get you started, here are the six most common (and most dangerous) types of phishing scams, and some useful tips on how you can defend your business against these.
1. Deceptive phishing
This is the most common type of phishing scam and it involves fraudsters impersonating reputable organizations to steal information or spread malware. These emails often convey a sense of urgency to scare victims into reacting quickly and doing exactly what the fraudsters want.
For instance, you receive an email that purports to be from Apple, PayPal, or your bank asking you to click on a link to verify your account. What you don’t know is that the link redirects to a fake login page. If you type in your credentials, the fraudsters can use this information to charge purchases to your credit card or commit identity theft.
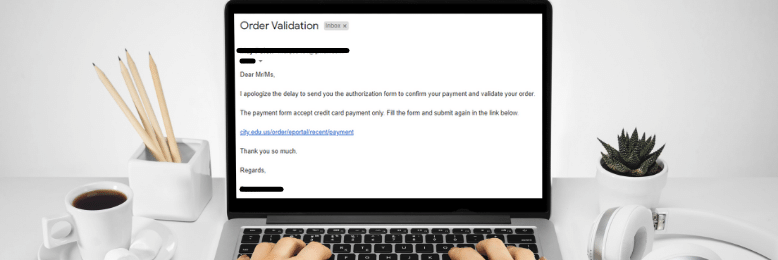
The success of a deceptive phishing email hinges on how harmless and legitimate it looks. If it closely resembles a piece of official correspondence from a trustworthy entity, then people won’t think twice about following its instructions. Therefore, you and your employees must be extra careful when opening unsolicited emails. Check if the sender’s email address matches the organization’s official domain name, which you can easily search online. Likewise, look out for poor grammar, generic greetings, and suspicious links and attachments — all of which are unmistakable indicators of a phishing email.
It’s worth noting, however, that checking the legitimacy of an unsolicited email can get tricky when you’re using a smartphone. You can’t instantly see the sender's email and hover over the attachment to preview its content. For these reasons, you may want to wait until you’re using a PC or laptop to view an unsolicited email.
2. Spear phishing
Phishing scams often cast a wide net, with emails usually sent out to thousands of recipients. However, some users rely heavily on personalization to be more effective. Enter spear phishing.
In this type of scam, fraudsters customize their emails with the target’s name, company, and other information to make it seem like the correspondence is from a known or trusted sender. Similar to deceptive phishing, the goal of spear phishing is to trick victims into clicking on an unscrupulous link or downloading a malicious attachment to obtain their personal data.
Given the amount of information needed to make a spear-phishing email as convincing as possible, fraudsters often lurk around social networking sites like LinkedIn where people’s information is readily available. For instance, LinkedIn users typically post about their jobs, their bosses, and the companies they work for, and that makes them easy targets for CEO fraud (which will be discussed in the next section).
To protect against this type of scam, you and your employees must avoid publishing personal or corporate information on social media. You can also invest in solutions that analyze inbound emails for known malicious content and prevent you from accidentally interacting with these.
3. CEO fraud
CEO fraud is a type of spear-phishing attack in which scammers impersonate a CEO or use a compromised email account of a high-ranking executive. They then trick an employee in accounting or HR into authorizing fraudulent wire transfers or disclosing confidential tax information.
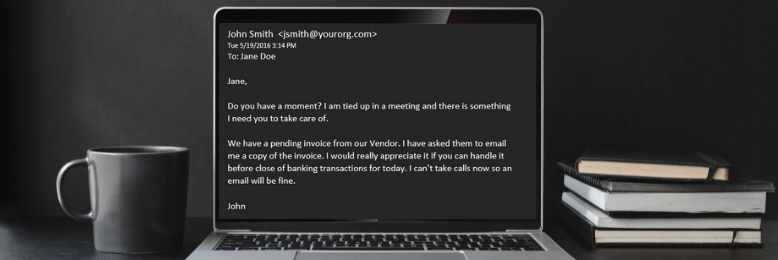
This type of scam works because executives are often not trained on their company’s security policies. The solution to this is to mandate all company personnel, including executives, to participate in regular security awareness training to avoid falling victim to social engineering attempts. You can also deploy multi-factor authentication solutions into your financial authorization processes so that no one can authorize payments via email alone.
4. Vishing
An email is undoubtedly a popular tool for phishing, but scammers sometimes turn to other media to perpetrate their attacks. Vishing (or voice phishing), for instance, takes place over the phone. A fraudster can set up a Voice over Internet Protocol phone system to mimic legitimate entities to coax victims into divulging sensitive information. So be extremely wary of calls asking you to verify your account information, provide your PIN, or answer your security questions.
But vishing is not only aimed at businesses. Elderly individuals as well as people with an aversion to technology are perhaps the most vulnerable targets, as they have little to no experience with these types of scams. A fraudster could call an elderly family member or relative and obtain your information from them. So it also pays to avoid sharing highly sensitive information even with the people closest to you and educate them about vishing attacks.
To protect against vishing attacks, set up caller ID and avoid answering calls from unknown phone numbers. Most importantly, never give out personal information over the phone, no matter how urgent or insistent the caller may sound, until you’ve verified the legitimacy of the call.
5. Smishing
Smishing leverages malicious text messages to trick victims into visiting malicious sites or handing over personal information. Smishing is particularly dangerous, as people are more inclined to trust a text message than an email.
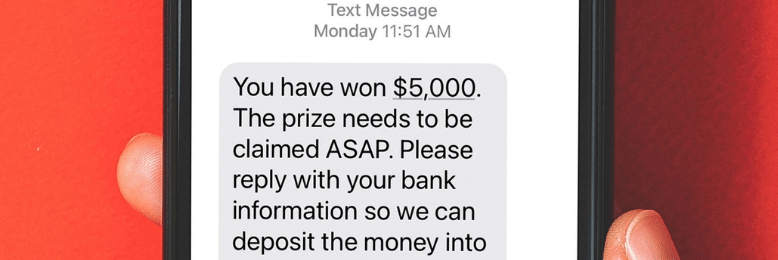
You and your employees can defend against smishing attacks by researching unknown phone numbers. If you have any doubts, contact the organization directly (using their official communication channels) to verify if the messages you receive are authentic.
6. Pharming
As users are becoming more aware of traditional phishing scams, some fraudsters are foregoing the idea of baiting their victims and are instead resorting to pharming. This involves installing malicious code on a computer or server and redirecting users to bogus sites without their knowledge or consent. Pharming doesn’t require victims to click on any link for them to be taken to a fraudulent site — they are redirected there automatically. The fraudsters would then have immediate access to any information entered on the site.
The best way to avoid pharming attacks is to double up on security. Invest in good security software — anti-malware programs and strong firewalls prevent, detect, and remove malicious files on your computers and systems. It’s also well worth encouraging employees to log in to HTTPS-protected sites only. Additionally, regularly check for open ports that might expose your systems to cyberattacks. It’s also well worth enlisting the help of IT experts to conduct network audits to check for vulnerabilities and keep your network and equipment updated, stable, and safe from threats.
Further reading:
Top 15 Cybersecurity Best Practices
Take the Next Step
To protect your business from these dangerous types of phishing attacks, partner with ITS. Together, we can create and implement a comprehensive cybersecurity strategy and a security awareness training program to protect your network and your distributed teams from increasingly sophisticated cyber threats. Call us today to schedule a FREE network audit and assessment.
Topics:
