Kronos Ransomware Attack: Lessons on Third-Party Risk Management
August 5th, 2022 | 4 min. read

Your cybersecurity game might be on point, but are your vendors on the same page?
That's a tough nut to crack, but it's a question you need to be asking yourself. Because in today's digital landscape, where you have a number of service providers with access to your data, it's not just your yard you should be concerned about.
To give you a better idea about what we mean, let's take a look at one of the most high-profile security incidents in 2021–the Kronos ransomware attack.
The attack hit Kronos' cloud service in December 2021 and affected over 8,000 employers, including hospitals. It prevented customers from processing payrolls, causing massive disruption and internal strife.
Things got so out of hand, that it took months before some companies regained access to their data. The situation prompted high-profile clients like Tesla, PepsiCo, Whole Foods, and the New York Metropolitan Transit Authority to pursue legal action seeking damages. Simply put, it all became a giant mess, –one that's admittedly hard to avoid. However, that doesn't mean there's nothing you can do to manage third-party risk.
At ITS, we are dedicated to helping businesses prevent such outcomes by sharing our insights and helping you understand what went wrong. In this article, we'll take a look at the following:
- How the Kronos ransomware attack happened;
- What you can do in a similar situation;
- How to manage third-party risk.
How the Kronos Ransomware Attack Happened
The payroll service company has kept pretty mum on all their public communications regarding the attack, so details are still scarce on exactly how the attack happened. However, Kronos did mention in a press release that it became aware of "unusual activity impacting UKG (United Kronos Group) solutions using Kronos Private Cloud" and determined it was a ransomware attack. From there, we can speculate on how things may have gone down.
In ransomware attacks, networks are infected with malicious software that locks or encrypts a victim's files, rendering them unable to access their data until the ransom is paid. However, there is no guarantee that the attackers will return access, and the ransoms can be worth a lot. In the case of Kronos, the company allegedly paid the ransom. We can assume they were forced into a situation where paying up was the cheapest and quickest way to regain access to their stolen data.
The workforce management company did not specify how their systems got infected. However, ransomware attackers typically use various methods like phishing, compromised user credentials, and even brute force to infiltrate security protocols. Those methods can allow an attacker to gain access to enterprise apps where they can deploy their malicious software.
What to Do When Your Vendor Gets Hacked
Just as you should have an incident response plan for when your business experiences a cyber-attack, you should also have a plan for when your vendors get hit. Don't get us wrong; we don't mean meddling in your service provider's recovery activity. However, a plan of action to safeguard critical operations tied with third parties is a must.
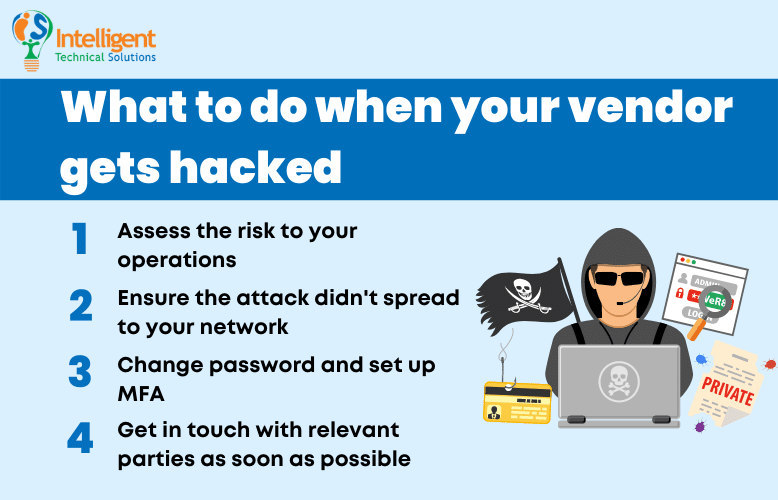
Take a look at some of the things you need to do when your vendor gets hacked:
Assess the Risk to Your Operations
The first thing you need to do when a vendor gets hit is to assess how the incident will impact your operations. Check whether any of your critical applications are tied with said vendor and try to find out how bad the damage will be if you lose service.
Ensure the Attack Didn't Spread to Your Network
Check whether the attack can spread to your network. While in the Kronos case, the attack was isolated to the company itself, there have been instances where attacks spread to the vendor's customers as well. Check your activity logs for any suspicious activity, and conduct a thorough scan of your network for possible breaches.
Change Passwords and Set Up MFA
Implement company-wide password changes and set up multi-factor authentication (MFA) immediately. That will prevent attackers from using stolen data, which can include passwords and other login credentials, from being used to break into your network. It's hard to determine what data the attackers were able to get from your vendor, so it would be better to err on the side of caution.
Get in Touch with Relevant Parties as Soon as Possible
Speed and information are key when dealing with any security breach. Make sure to inform your IT security team or your managed service provider (MSP) of issues like this as soon as possible. It will help them act faster to protect your network, assess the damage, and hopefully, resolve issues that may come up.
How to Manage Third-Party Risk
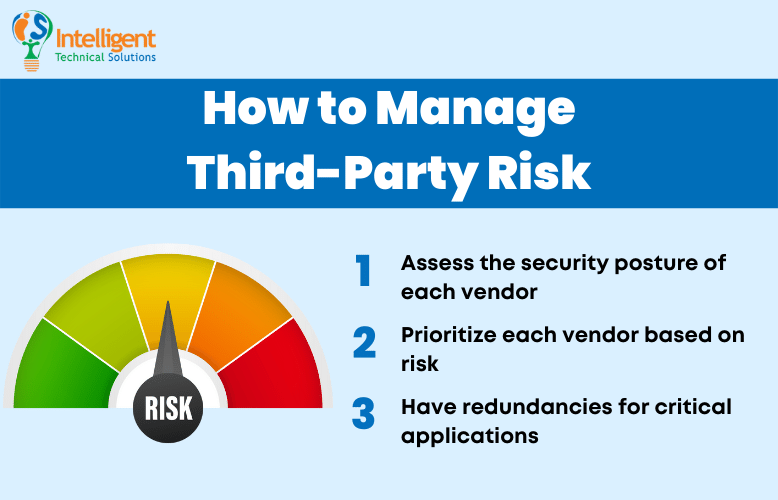
There's only so much you can do to manage third-party risk. After all, you have no control over how an external company manages its cybersecurity. But that doesn't mean there's nothing you can do to manage your exposure. Check out some of the things you can do to help manage third-party risk:
Assess the Security Posture of Each Vendor
When dealing with a vendor, it's vital to ask the right questions. Always keep their cybersecurity posture at the top of your mind. If possible, try to assess what measures they have in place against cyber threats, what security standards they comply with, and what guarantees they offer should their service fail.
Prioritize Each Vendor Based on Risk
After you determine the risks associated with each vendor, you will then be able to categorize them based on how important they are to your business and what potential threats they may pose. That gives you a better picture of your portfolio of third-party services. It will allow you to address any critical issues before things go south and determine whether switching to another vendor would be better for you.
Have Redundancies for Critical Applications
When possible, employ redundancies for mission-critical operations. That will allow you to recover your bearings in case of a service outage from your vendors, which means if a critical app failure occurs, a workaround is already in place to minimize disruption to your operations.
Ready to Act When Your Vendor Gets Attacked?
The Kronos ransomware incident serves as a good reminder that your network isn't the only one you should worry about. Cyber threats can shut down third-party services that can disrupt some of your critical operations, too. Knowing how to mitigate the risks and what to do in case your vendor is attacked can help mitigate the impact.
The moment a service provider notifies you that they've been compromised, make sure to do the following:
- Assess the Risk to Your Operations
- Ensure the Attack Didn't Spread to Your Network
- Change Passwords and Set Up MFA
- Get in Touch with Relevant Parties as Soon as Possible
At ITS, we are committed to helping businesses manage tech risks and improve their cybersecurity posture by sharing our insights. Learn how MSPs deal with ransomware by checking out our article: 4 Security Measures that MSPs Employ to Prevent Ransomware Attacks. After reading, you'll be able to glean the steps that experts take so you can apply them to your network.
Mark Sheldon Villanueva has over a decade of experience creating engaging content for companies based in Asia, Australia and North America. He has produced all manner of creative content for small local businesses and large multinational corporations that span a wide variety of industries. Mark also used to work as a content team leader for an award-winning digital marketing agency based in Singapore.
Topics:
