Microsoft is Moving Away From Basic Authentication
August 11th, 2022 | 4 min. read
You might have already heard, but Microsoft wants you to say goodbye to Basic Authentication. Simply put, they want everyone around the world to ditch the old username and password combo for logging in and adopt multi-factor authentication (MFA) instead. It's a step that could significantly reduce the number of security incidents globally. However, it also has the potential to cause work disruptions and outages, especially if you're not prepared for it.
ITS is an IT support company dedicated to helping businesses like yours adapt and make the most out of your Microsoft environment. In this article, we'll help you prepare for the changes coming this October 2022 that aim to disable Basic Authentication for Microsoft products. To do that, we'll dive into the following:
- Why is Microsoft deprecating Basic Authentication?
- How will the changes impact your business?
- Which Microsoft services are affected?
- What do you need to prepare for a seamless transition?
Why is Microsoft Deprecating Basic Authentication?

Basic Authentication refers to a simple challenge and response mechanism in which a server can request authentication information (in this case, a user ID and password) from a client before granting access to data. It's an age-old method of verifying a user's credentials and has grown wholly unreliable.
The user ID and password combo is so easy to compromise that Microsoft's Chief Information Security Officer (CISO) has once said: "Hackers don't break in; they log in." In fact, the tech giant even revealed that they recorded a whopping 579 password attacks every second—that's 18 billion every year.
"This is a global change that Microsoft is making, and they're making it for a reason," says Rob Schenk, Chief Experience Officer for ITS. "Microsoft is trying to kill an old legacy protocol to improve overall security for everybody," he adds. You can think of it as the tech company's effort to cut the problem of credential compromise at the root, which can significantly reduce the number of successful phishing and malware attacks.
How Will the Changes Impact Your Business?
According to Schenk, "If you didn't prepare for this change when it goes into effect, you have the potential for business interruption."
That's because some of your users might no longer be able to check their emails and communicate on their mobile devices once it rolls out. You will have to do some updates and reconfigurations to get them back on track.
In addition, you might have network devices or a line of business applications using old methodologies. If you disable basic authentication without preparation, those devices and apps might stop working altogether. It has the potential to cause either a minor inconvenience or a major crisis.
Which Microsoft Services are Affected?
According to Microsoft, the changes will affect several messaging protocols and existing applications in different ways. Learn more about them below:
POP, IMAP, and SMTP AUTH
Apps that send, read, or otherwise process email using POP, IMAP, and SMTP AUTH will be able to keep the same protocol but need to implement secure modern authentication. You will need to work with your vendor or affected clients to update any app using said protocols.
Exchange ActiveSync (EAS)
If your mobile device is set up to use EAS to access your email, Microsoft recommends moving to Outlook for iOS and Android instead. Not only does the app support modern authentication natively, but it also fully integrates Microsoft Enterprise Mobility + Security (EMS). That allows you to enable conditional access and app protection capabilities for better security for your users and your corporate data.
Exchange Online PowerShell
For administrators still using the old remote PowerShell connection method or the older Exchange Online Remote PowerShell Module, Microsoft advises switching to Exchange Online V2 PowerShell (EXO V2). It uses modern authentication and MFA to connect all Exchange-related PowerShell environments in Microsoft 365. The new version also enables more advanced features that will make managing your Exchange Online settings much easier.
Exchange Web Services (EWS)
Microsoft has already stopped providing feature updates for EWS, urging users to instead switch to using Microsoft Graph. However, there may still be some apps that cannot successfully move to Graph. In those cases, EWS already fully supports modern authentication.
Outlook
Older versions of Outlook, such as 2007 and 2010, cannot use modern authentication. That means that come October; you will no longer be able to connect to them. On the other hand, Outlook 2013 requires you to toggle a setting that enables modern authentication, allowing you to use it post-change without issues.
What Do You Need to Prepare for a Seamless Transition?
It's better to get ahead of this change than to wait for it to roll out and see if something in your system breaks. "You definitely want to get ahead of this as much as possible and do your due diligence to make sure that these updates and reconfigurations happen," Schenk says.
To do that, you first need to figure out which apps and protocols will be affected. Determine which ones need updating, reconfiguring, or replacing with one that supports modern authentication. You can find that out by using several methods:
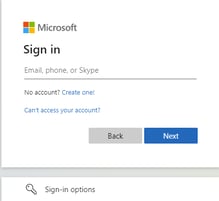
Check the Authentication Dialog - Observe the dialog box presented when the user logs in. If an app uses modern authentication, it will display a web-based login page:
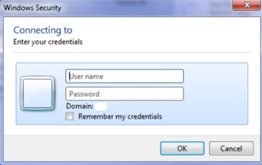
However, if not, you'll see a dialog credential modal box instead:
Check the Message Center - Microsoft started sending Message Center posts to tenants that summarize their usage of Basic Authentication in 2021. A quick check will allow you to see how many unique users used Basic Authentication in the previous month, and which protocols they used.
Check the Azure Active Directory Sign-In Report - For the most in-depth view of your Basic Authentication usage, you can check the Azure AD Sign-In report available in the Azure Portal. The sign-in logs provide a lot of information, including username, application, client app, device—and now—user agent. However, large customers might need to aggregate this data into a report to make it easier to view and understand. You can do that via Azure Monitor, Excel, Microsoft Graph API, or a security information and event management (SIEM) system.
Ready to Say Goodbye to Basic Authentication?
Microsoft moving away from Basic Authentication can do wonders in reducing the number of phishing and malware attacks worldwide. However, it's a big step that can potentially lead to disruptions because it will affect several messaging protocols and existing applications in different ways.
Versions of POP, IMAP, SMTP AUTH, EAS, Exchange Online PowerShell, EWS, and Outlook may require some updates and reconfiguration to work properly come October 2022. Failing to prepare ahead of time may lead to business interruptions that balloon into a crisis. So staying ahead of this change will help you ensure a seamless transition.
At ITS, we are dedicated to helping businesses like yours secure and optimize your technology. If you need help implementing modern authentication, check out our article on How to Implement MFA for Email Exchange Servers.
Mark Sheldon Villanueva has over a decade of experience creating engaging content for companies based in Asia, Australia and North America. He has produced all manner of creative content for small local businesses and large multinational corporations that span a wide variety of industries. Mark also used to work as a content team leader for an award-winning digital marketing agency based in Singapore.
Topics:
